Signer authentication + data integrity + non-repudiation = Trust
What are digital signatures?
The term digital signature is used to refer to a category of e-signatures which are created using Public Key Cryptography (PKC). The terminology is often confusing, as an example the EU eIDAS Regulation has used terms such as “advanced electronic signatures” and “qualified electronic signatures” in an effort to be technology-neutral. However, practically the only way to implement these is to use digital signature based on PKI.
Download our free Guide to choosing the right type of e-signature

What security is provided by digital signatures?
The three core security services provided by digital signatures are:

Signer authentication
Proof of who actually signed the document i.e. digital signatures linking the user’s signature to an actual identifiable entity.

Data integrity
Proof that the document has not been changed since signing. The digital signature depends on every binary bit of the document and therefore can’t be re-attached to any other document.

Non-repudiation
The signer should not be able to falsely deny having signed. That is, it should be possible to prove in a court that the signer in fact created the signature. Conversely it should not be possible to falsely claim that someone signed a document when they did not.
All the evidence required to deliver the above security services should be available directly from the signature, without requiring referral to audit trails and service provider logs.
How do digital signatures work?
The most common way of creating a digital signature is to use Public Key Cryptography (PKC). The systems used to deliver PKC are called Public Key Infrastructures (PKI). At a basic level digital signature solutions require each user to have a public and private key pair which are mathematically linked. The private key remains under the owner’s sole control and is used to sign. The signing process creates a crypto code, which is embedded into the document.
Click here for more details on Basics of Digital Signatures & PKI
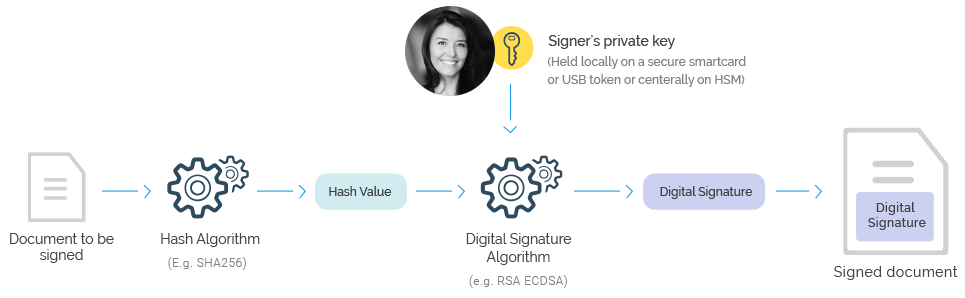
At the time of verification the signer’s public key is used to unwrap the digital signature code and compare it with the document to ensure a match:
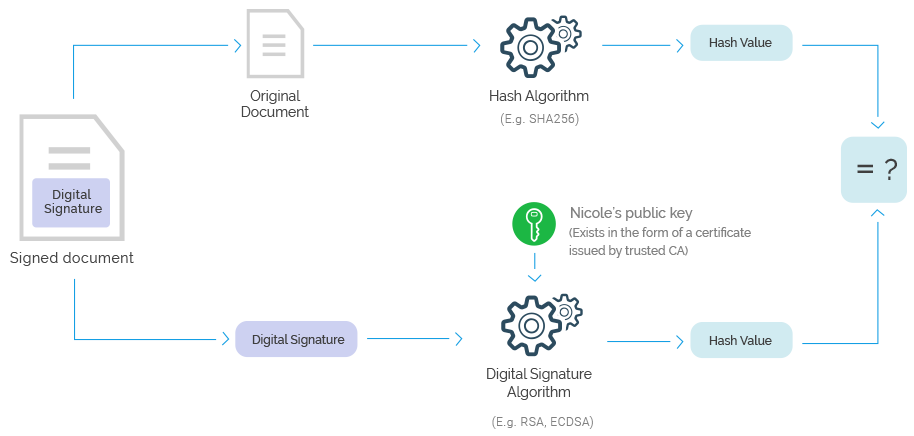
What is the security of digital signatures based on?
A PKC based digital signature is based on the following security principles:
There is no way for anyone to work out someone’s private key from their public key. This is because PKC is based on hard mathematical one-way problems, e.g. like factoring a large number which is the product of two primes.
The private key is under the sole control of the owner. This can be held locally by the user (e.g. on a secure smartcard/USB token), in this case the signing process is referred to as “local signing”. Or the private key can be held centrally in a Hardware Security Module (HSM) – a tamper-protected hardware component. In this case the signing process is referred to as “remote signing”. The key is only released to the user after successful authentication using either single or multi-factor authentication.

There is no way for anyone to work out someone’s private key from their public key. This is because PKC is based on hard mathematical one-way problems, e.g. like factoring a large number which is the product of two primes.
The private key is under the sole control of the owner. This can be held locally by the user (e.g. on a secure smartcard/USB token), in this case the signing process is referred to as “local signing”. Or the private key can be held centrally in a Hardware Security Module (HSM) – a tamper-protected hardware component. In this case the signing process is referred to as “remote signing”. The key is only released to the user after successful authentication using either single or multi-factor authentication.
What’s better? E-Signatures or Digital Signature?
Generally the term e-signature is used to refer to the person’s hand-signature mark drawn on a document. A basic e-signature mark like this provides no security as it can be easily copied/pasted as well as the document can be changed without detection. However it does provide quick human recognition that a person has signed the document.
Therefore it’s best to combine e-signature marks (often referred to as signature appearance) with strong digital signatures using unique PKC keys under the sole control of the signer. This achieves the best of both of worlds, i.e. easy recognition that someone has signed with strong cryptographic protection that digital signatures provide.
Therefore it’s best to combine e-signature marks (often referred to as signature appearance) with strong digital signatures using unique PKC keys under the sole control of the signer. This achieves the best of both of worlds, i.e. easy recognition that someone has signed with strong cryptographic protection that digital signatures provide.
What are Certificate Authorities (CAs) and why are they needed?
Before using someone’s public key to verify a signature, you need assurance that it indeed belongs to them. The CA’s role is to issue digital certificates to entities within a PKI system which proves that a particular public key belongs to a particular person – so you can say digital certificates bind the person’s identity with their public key. This binding is secured by the CA using a digital signature using the CA’s own private key.
There are many CAs around the world, they can be enterprise-based, industry-based, national (e.g. linked to e-ID card schemes) or publicly available over the internet. In case of PDF documents, the ubiquitous Adobe PDF Reader comes with a list of default CAs.
What are Certificate Authorities (CAs) and why are they needed?
Before using someone’s public key to verify a signature, you need assurance that it indeed belongs to them. The CA’s role is to issue digital certificates to entities within a PKI system which proves that a particular public key belongs to a particular person – so you can say digital certificates bind the person’s identity with their public key. This binding is secured by the CA using a digital signature using the CA’s own private key.
There are many CAs around the world, they can be enterprise-based, industry-based, national (e.g. linked to e-ID card schemes) or publicly available over the internet. In case of PDF documents, the ubiquitous Adobe PDF Reader comes with a list default of CAs.
Standards based on digital signatures
Digital signatures are inside the heart of many modern standards which ensures more trust and security of data and documents. Some of these are technical standards managed by IETF e.g. PKCS#7/CMS standards and some cover legal and business needs like eIDAS and standards bodies like ETSI and CEN.
SigningHub supports all important signature standards including PAdES, XAdES and CAdES. This includes advanced profiles like *AdES-X-L and *AdES-A.

With SigningHub we have reduced approval time significantly and can ensure EU compliance. We promote the use of innovative, useful cloud technologies and we have found just that with SigningHub.

Juraj Zelenay
Program Group Manager, Digital Tools, EuroCloud Europe
With SigningHub we have reduced approval time significantly and can ensure EU compliance. We promote the use of innovative, useful cloud technologies and we have found just that with SigningHub.

Juraj Zelenay
Program Group Manager, Digital Tools, EuroCloud Europe